A sextant is an instrument used to measure the angle between any two visible objects. Its primary use is to determine the angle between a celestial object and the horizon which is known as the altitude. Making this measurement is known as sighting the object, shooting the object, or taking a sight. The angle, and the time when it was measured, can be used to calculate a position line on a nautical or aeronautical chart. A common use of the sextant is to sight the sun at noon to find one's latitude. See celestial navigation for more discussion. Since the sextant can be used to measure the angle between any two objects, it can be held horizontally to measure the angle between any two landmarks which will allow for calculation of a position on a chart. A sextant can also be used to measure the Lunar distance between the moon and another celestial object (e.g., star, planet) in order to determine Greenwich time.
The scale of a sextant has a length of 1⁄6 of a full circle (60°); hence the sextant's name (sextāns, -antis is the Latin word for "one sixth", "εξάντας" in Greek). An octant is a similar device with a shorter scale (1⁄8 of a circle, or 45°), whereas a quintant (1⁄5, or 72°) and a quadrant (1⁄4, or 90°) have longer scales.
Sir Isaac Newton (1643–1727) invented the principle of the doubly reflecting navigation instrument (a reflecting quadrant - see Octant (instrument)), but never published it. Two men independently developed the octant around 1730: John Hadley (1682–1744), an English mathematician, and Thomas Godfrey (1704–1749), a glazier in Philadelphia. The octant and later the sextant, replaced the Davis quadrant as the main instrument for navigation.
Advantages
Like the Davis quadrant (also called backstaff), the sextant allows celestial objects to be measured relative to the horizon, rather than relative to the instrument. This allows excellent precision. However, unlike the backstaff, the sextant allows direct observations of stars. This permits the use of the sextant at night when a backstaff is difficult to use. For solar observations, filters allow direct observation of the sun.
Since the measurement is relative to the horizon, the measuring pointer is a beam of light that reaches to the horizon. The measurement is thus limited by the angular accuracy of the instrument and not the sine error of the length of an alidade, as it is in a mariner's astrolabe or similar older instrument.
The horizon and celestial object remain steady when viewed through a sextant, even when the user is on a moving ship. This occurs because the sextant views the (unmoving) horizon directly, and views the celestial object through two opposed mirrors that subtract the motion of the sextant from the reflection.
The sextant is not dependent upon electricity (unlike many forms of modern navigation) or anything human-controlled (like GPS satellites). For these reasons, it is considered an eminently practical back-up navigation tool for ships.
Anatomy of a sextant

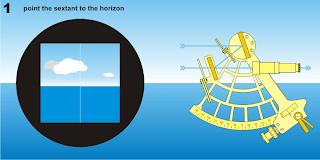
Using the sextant to measure the
altitude of the Sun above the horizon
The index arm moves the index mirror. The indicator points at the arc to show the measurement. The body ties everything together.
There are two types of sextants. Both types can give good results, and the choice between them is personal.
Traditional sextants have a half-horizon mirror. It divides the field of view in two. On one side, there is a view of the horizon; on the other side, a view of the celestial object. The advantage of this type is that both the horizon and celestial object are bright and as clear as possible. This is superior at night and in haze, when the horizon can be difficult to see. However, one has to sweep the celestial object to ensure that the lowest limb of the celestial object touches the horizon.
Whole-horizon sextants use a half-silvered horizon mirror to provide a full view of the horizon. This makes it easy to see when the bottom limb of a celestial object touches the horizon. Since most sights are of the sun or moon, and haze is rare without overcast, the low-light advantages of the half-horizon mirror are rarely important in practice.
In both types, larger mirrors give a larger field of view, and thus make it easier to find a celestial object. Modern sextants often have 5 cm or larger mirrors, while 19th century sextants rarely had a mirror larger than 2.5 cm (one inch). In large part, this is because precision flat mirrors have grown less expensive to manufacture and to silver.
An artificial horizon is useful when the horizon is invisible. This occurs in fog, on moonless nights, in a calm, when sighting through a window or on land surrounded by trees or buildings. Professional sextants can mount an artificial horizon in place of the horizon-mirror assembly. An artificial horizon is usually a mirror that views a fluid-filled tube with a bubble.
Most sextants also have filters for use when viewing the sun and reducing the effects of haze.
Most sextants mount a 1 or 3 power monocular for viewing. Many users prefer a simple sighting tube, which has a wider, brighter field of view and is easier to use at night. Some navigators mount a light-amplifying monocular to help see the horizon on moonless nights. Others prefer to use a lit artificial horizon.
Professional sextants use a click-stop degree measure and a worm adjustment that reads to a minute, 1/60 of a degree. Most sextants also include a vernier on the worm dial that reads to 0.2 minute. Since 1 minute of error is about a nautical mile, the best possible accuracy of celestial navigation is about 0.1 nautical miles (200 m). At sea, results within several nautical miles, well within visual range, are acceptable. A highly-skilled and experienced navigator can determine position to an accuracy of about 0.25-nautical-mile (460 m).[1]
A change in temperature can warp the arc, creating inaccuracies. Many navigators purchase weatherproof cases so that their sextant can be placed outside the cabin to come to equilibrium with outside temperatures. The standard frame designs (see illustration) are supposed to equalise differential angular error from temperature changes. The handle is separated from the arc and frame so that body heat does not warp the frame. Sextants for tropical use are often painted white to reflect sunlight and remain relatively cool. High-precision sextants have an invar (a special low-expansion steel) frame and arc. Some scientific sextants have been constructed of quartz or ceramics with even lower expansions. Many commercial sextants use low expansion brass or aluminium. Brass is lower-expansion than aluminium, but aluminium sextants are lighter and less tiring to use. Some say they are more accurate because one's hand trembles less.
Aircraft sextants are now out of production, but had special features. Most had artificial horizons to permit taking a sight through a flush overhead window. Some also had mechanical averagers to make hundreds of measurements per sight for compensation of random accelerations in the artificial horizon's fluid. Older aircraft sextants had two visual paths, one standard and the other designed for use in open-cockpit aircraft that let one view from directly over the sextant in one's lap. More modern aircraft sextants were periscopic with only a small projection above the fuselage. With these, the navigator pre-computed his sight and then noted the difference in observed versus predicted height of the body to determine his position.
After a sight is taken, it is reduced to a position by following any of several mathematical procedures. The simplest sight reduction is to draw the equal-elevation circle of the sighted celestial object on a globe. The intersection of that circle with a dead-reckoning track, or another sighting gives a more precise location.
Care
A sextant is a delicate instrument. If dropped, the arc might bend. After one has been dropped, its accuracy is suspect. Recertification is possible with surveying instruments and a large field, or with precision optical instruments. Repair of a bent arc is generally impractical.
Many navigators refuse to share their sextants, to ensure that their integrity is traceable.
Most sextants come with a neck-lanyard; all but the cheapest come with a case. Traditional care is to put on the neck lanyard before removing the sextant from its case, and to always case the sextant between sights. A used sextant lacking a case is very likely to be damaged.
To avoid worries about bent arcs, serious navigators traditionally buy their sextants new. Common wisdom is that a used sextant is probably bent. Bauer disagrees:[2]
I don't subscribe to the old maxim of maritime philosophers about never buying a used sextant. The implication is that using them ruins them. This is untrue. Sextants wear out very slowly and they usually get treated with utmost gentleness and even reverence. Damage is not hard to detect if the instrument is examined intelligently. I think I would modify that old rule to read: Don't buy a used sextant for more than half the retail cost of the least expensive, new, full-sized instrument—unless the money saved is critical to your budget.... There are many good used instruments around and by exercising caution and avoiding hasty deals, one can end up with a sound instrument for a lot less money.
Adjustment
Due to the sensitivity of the instrument it is easy to knock the mirrors out of adjustment. For this reason a sextant should be checked frequently for errors and adjusted accordingly.
There are four errors that can be adjusted by the navigator and they should be removed in the following order.
- Perpendicularity error
- This is when the index mirror is not perpendicular to the frame of the sextant. To test for this, place the index arm at about 60° on the arc and hold the sextant horizontally with the arc away from you at arms length and look into the index mirror. The arc of the sextant should appear to continue unbroken into the mirror. If there is an error then the two views will appear to be broken. Adjust the mirror until the reflection and direct view of the arc appear to be continuous.
- Side error
- This occurs when the horizon glass/mirror is not perpendicular to the plane of the instrument. To test for this, first zero the index arm then observe a star through the sextant. Then rotate the tangent screw back and forth so that the reflected image passes alternately above and below the direct view. If in changing from one position to another the reflected image passes directly over the unreflected image, no side error exists. If it passes to one side, side error exists. The user can hold the sextant on its side and observe the horizon to check the sextant during the day. If there are two horizons there is side error; adjust the horizon glass/mirror until the stars merge into one image or the horizons are merged into one.
- Collimation error
- This is when the telescope or monocular is not parallel to the plane of the sextant. To check for this you need to observe two stars 90° or more apart. Bring the two stars into coincidence either to the left or the right of the field of view. Move the sextant slightly so that the stars move to the other side of the field of view. If they separate there is collimation error.
- Index error
- This occurs when the index and horizon mirrors are not parallel to each other when the index arm is set to zero. To test for index error, zero the index arm and observe the horizon. If the reflected and direct image of the horizon are in line there is no index error. If one is above the other adjust the index mirror until the two horizons merge. This can be done at night with a star or with the moon.